All You Need To Know About Cryptography In Blockchain
Cryptography is the foundation of blockchain. This article is an introduction to the topic as well as an argument about its importance!
What is Cryptography?
Cryptography in Blockchain or even in general is a tricky concept. Cryptography is made up of two ancient Greek terms, Kryptos and Graphein, the former term meaning “hidden” and the latter being “to write”. Hence, cryptography means the art of writing and solving codes.
Cryptography is the method of developing techniques and protocols which prevent third parties from accessing and gaining knowledge of the data from private messages during peer-to-peer communication. In short, cryptography is a method of storing and transmitting data in a particular form so that only those for whom it is intended can read and process it, hence it can also be used for authentication purposes.
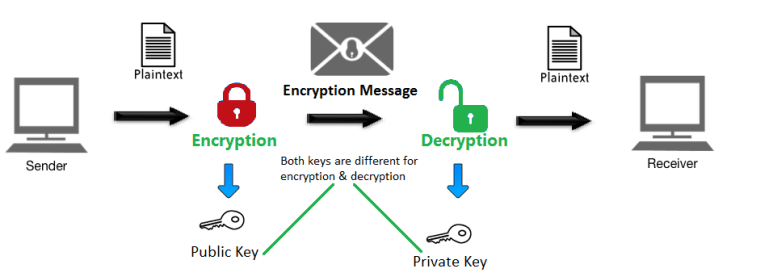
Why Cryptography?
Blockchain operates with a decentralized, peer-to-peer network model since there is no single node, and nodes don't have to trust one another in this new technology. So, blockchain has to ensure appropriate safeguards for all transaction information on unsecured channels while maintaining transaction integrity. Therefore, cryptography becomes an essential requirement for blockchain to safeguard user transaction information and privacy alongside ensuring data consistency.
The primary applications of cryptography focuses on ensuring the security of participants and transactions, safeguarding against double-spending, and lack of influence on central authorities and operations. Blockchain applications leverage the concept of real-world signatures by leveraging cryptography techniques along with encryption keys to provide the necessary security, hence ensuring the integrity of information.
This article is part of a series of articles around blockchain, web3, and terminologies around it. To start with Cryptography, there is the assumption that you should be familiar about Blockchain and Smart contracts to understand why we need Cryptography in a Blockchain decentralised ecosystem. If you haven't read about about it, you can refer to BlockChain and Smart Contracts to get started. In the previous article we covered:
- What is blockchain and smart contracts?
- How smart contract works?
- Practical applications of smart contracts.
Terminologies in Cryptography
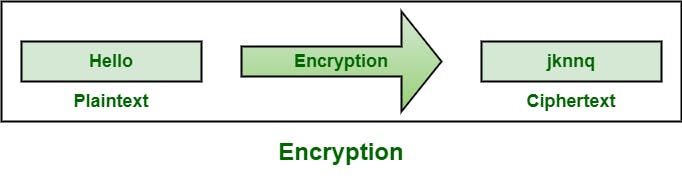
Encryption - It is a method by which information in plain text is converted into cipher text (secret code) in order to hide its true meaning. Here's an image of how this looks:
Decryption - It's the opposite of encryption. It's the process of converting encrypted data back to it's original form.
Cipher - In cryptography, it's a series of algorithms to perform encryption or decryption. These algorithms define a series of steps defined to be followed in sequence. For example, say shifting plain texts a certain no of places for better visibility, say with a shift of 2 , A would be C and B would be D and so on...
Keys - Keys in cryptography contain certain information used to encrypt and decrypt information. Based on the encryption type, either a single secret key is used to encrypt and decrypt information or a public/private pair would be used. In case of a public/private key pair, thepublic key is used to encrypt the information and private keys are used to decrypt the information.
Types of Cryptography
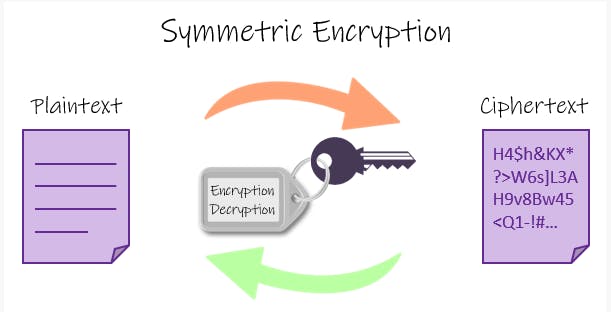
Symmetric-Key Cryptography - This is also known as secret-key cryptography. In this method, a single key is used for both encryption and decryption. One of the problems in this type of encryption is transferring the key securely between the sender and receiver. Refer to the image given below for your reference:
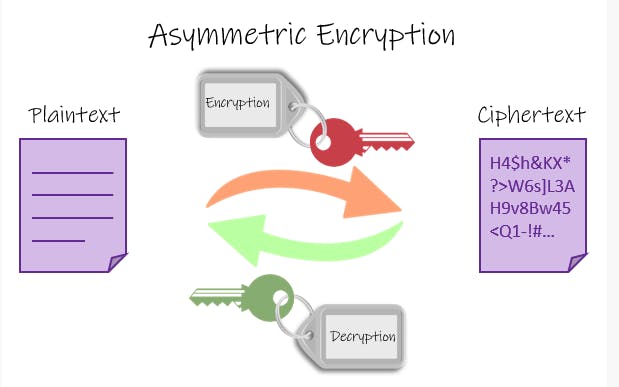
Asymmetric-Key Cryptography - This is also known as public-key cryptography. This method consist of a pair of keys, an encryption key and a decryption key also named public and private key respectively. Hence, public key is used to encrypt a piece of information while a a private key is used to decrypt the information. Refer to the image given below:
Hash function - Hash functions generates a unique identifier for any set of inputs. Basically, it is a process that takes plain text data of any size and converts it into a unique ciphertext of a specific length. Hence, no two pieces of content will have the same hash digest, and in case if the content changes even slightly the hash digest changes as well. Here's a basic illustration of how hash functions work:
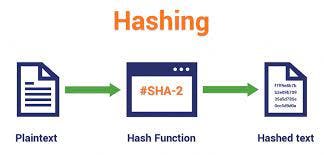
How does Hashing works?
Hashing a message means we will take a string of data of any size as our input and run it through algorithms that generate an output of a fixed length. In case if the input data is large , it is broken into smaller blocks of equal size. However if the input data is small, then paddings (1's or 0's) can be used to fill it out. These blocks are further run through the algorithm which results in the generation of an output of a fixed length. Refer to the image below:
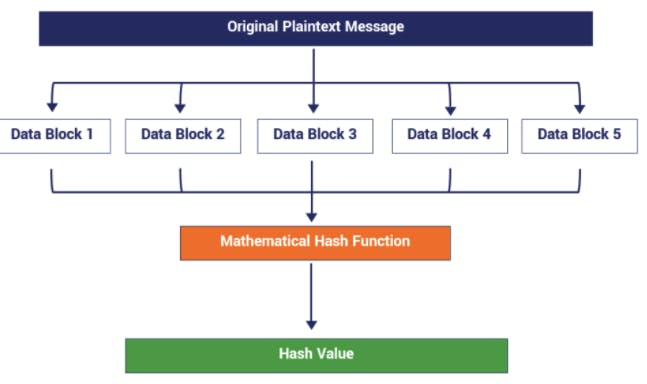
Hash Functions with examples
There are various different types of hashing algorithms. Let us consider a common input and check however different hash algorithms generate outputs of a fixed length. Run the following code in your console:
A blockchain is a public database
that is updated and shared across
many computers in a network.
- Secure Hash Algorithm (SHA) - This family of hashes contains
SHA-1,SHA-2andSHA-3. However, the most commonly used hashing algorithm isSHA-256of theSHA-2family. The output forSHA-256, the input would be as shown below and even if the input length is changed the output will be of a fixed length itself. Run the following code to check this:
33606711a0e8b96b605352edbab973752e8067241016bfc9ebced90851024a3e
- What if we run the same input through
SHA-512? The output will be of a 512-bit hexadecimal string instead of 256 bit. Run the following code to verify this:
43cf5b2f5a99112d19f279fee413047daee2278968d52de40fd18548
a507818e01df76743224c16f76387b3ccc5c6acc6eab09d4dbfe989104b473aa76566b
- Message Digest (MD) - This includes
MD2,MD4,MD5, andMD6. For quite a long time,MD6used to be considered a go-to algorithm but it's now considered as broken because it can collide in the wild. Run the following snippet in your console:
5DFDKL3139752B45TGE878A15216598
- There are other hashing algorithms as well, however the SHA family is the most prominently used one.
Hashing vs Encryption
From the flow diagram which is depicted above, it looks like both the hash functions and encryption are the same thing, but in reality they aren't. If someone talks about decrypting the hash value, then they don't know what they are talking about. :-P
The hash function is a one way function, whereas encryption is a two way function. ie. in the hash function, we can convert an input into an readable string of digits but not the other way around. While encrypting, the one who has the key can display the output.
Why does blockchain uses cryptography?
Here are some reasons why blockchain uses cryptography:
- Deterministic - A strong cryptographic algorithm such as hash functions are deterministic in nature. ie. for any input, the resulting output length is fixed.
- Collision resistance - With strong hashing algorithms such as SHA-256 and SHA-512, it's almost impossible to find the same hash for the same enciphered text.
- Avalanche Effect - This means that a slight change in the input results in a completely different output. ie. a change in just one bit of the input results in a change to half of the bits of its hash.
- Irreversible - With a strong cryptographic algorithms such as hash functions, reverse engineering is not possible, i.e. we cannot generate the input by having the output and the hash function.
Conclusion
As you can see from this article, cryptography is the core of blockchain technology. It utilises advanced mathematical codes for the storage and transmission of data values in secure formats. As a result of which it ensures that only the individuals for whom the transaction or data is intended can obtain, read and process the transaction or data and verify the authenticity of participants and the transaction making it a safe and secure option
What's next?
We started with the blockchain and the underlying mechanism of how it works. It's time to start interacting with blockchain and web3 is a gateway to it. In the next article, we will discuss Web3, it's terminologies and technology layers in it.
This article is part of Research & Development work being done by Pushkar Kumar, Suresh Konakanchi, and Ruchika Gupta. We will be covering a series of articles along with open source projects around blockchain, smart contracts, and web3 in general. Here is the list of all the articles that you can follow to start with Blockchain and write your first contract:

